

Within the past month (around mid-October 2013), a new virus, called CryptoLocker, has struck. Once it has struck your system, there are only two ways to recover your data: either pay the hacker or restore a backup. The virus encrypts Windows user data with 2048-bit RSA keys which would take the lifetime of humans on earth to crack with brute force. The virus installs a public encryption key on your computer, retaining the private key on their server. Without access to the private key, there is no way to decrypt the data (see Malwarebytes' description of the problem. Paying criminals to unlock your data only makes the criminal activity more attractive, so it is in all of our best interests to keep ourselves safe.
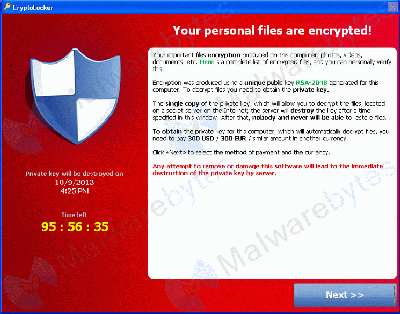
CryptoLocker message (click for larger picture)
The only way to get your decrypt key back is, within 3 days of infection, to pay the thieves $300 (variants are spreading, so price will vary). The ransom has to be paid in bitcoin or pre-paid voucher. So far, they do appear to be sending the decrypt keys, except that the FBI and others are attempting to take down their servers, so it is possible that the FBI could destroy the only copy of your decrypt keys. If you don't pay within three days, they have a second program that will get your data back within about a week, but it currently costs about $1,200. The virus is targeted at businesses who are more likely to be able to pay the ransom for data, and have a compelling need to do so.
If you can see your backup files while your computer is running (a "hot" backup), those may be encrypted also, so you won't have a working backup. Even worse, if you have a "cold" backup (one that you can't see while running Windows), your backup can overwrite good files with encrypted files, rendering your backup useless.
Fortunately, there are some precautions you can take to protect yourself, but they take thought and planning.
If you are a home user, there is a decent option to protect yourself without a lot of work from you. Head out to CryptoPrevent and for $15 you can protect all the computers within your household. They provide automatic updates as needed to keep your definitions current. As rapidly as this thing is morphing, don't even think about downloading the current, free, version and thinking you are protected. Very few home users have the attention to detail necessary to manually download all the updates.
In addition, home users need to maintain cold backups with versioning. If your computer system can see the backup files, so can the virus. If it encrypts your backup, you are sunk. The easiest way to provide a cold backup with versioning (keeps older versions of changed files), is to use one of the inexpensive, commercial backup providers like Mozy or Carbonite. A Networked Access Storage (NAS) device can also provide protection as long as the username/password you use on a daily basis has no access to the NAS. Create a user account you don't every use to access the Internet or receive email to access the NAS for backups. Set access to the backup drive so only the backup account can access it. This way, if you do get the virus, it won't contaminate your backups.
For companies, things get a bit more complicated. First and foremost, every workstation and server needs to have the execution protections that CryptoPrevent installs updated on every workstation and server. Servers can roll out the execution preventions via Group Policy, but someone needs to watch for changes in where the virus attempts to install itself. Next, the system needs versioned cold backups. Fortunately, this is not too difficult as most servers have a separate backup account that can be used.
Whatever you do, do not neglect protecting yourself. The virus is spreading, more hackers are grabbing the code and creating copy-cat viruses, the virus is increasing its attack-surface (more kinds of data are being encrypted) so that what works today to keep you safe, may not work tomorrow. This is the first virus we have had that was so carefully constructed that there is no way to repair an infected computer.
The BleepingComputer website is an excellent source for discussion of malware. Their frequently updated CryptoLocker page has lots of great information.

Visit the CIPCUG user group website for the best self-help resource in the county.